Brute-Force Attack is a attack that happens when the attacker doing trial-and-error to find the authentication username and password of the web application. Here, we will try to demonstrate using brute-force attack to attack a system. And we will also learn how to prevent our system from being brute-force
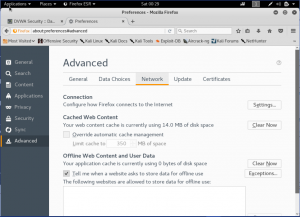
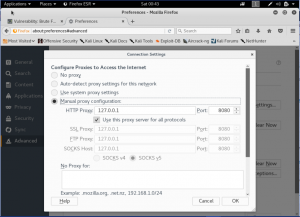
First, open preferences of the web browser, the set the proxy into 127.0.0.1 port 8080
Now, open burp-suite. This is the tool we will use to do brute-force. Open the proxy tab and make sure to turn off the intercept first. We will turn this on later
Open again the browser, and set the DVWA security into low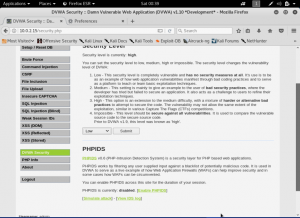
Now, we start by go to the brute-force page and then turning on the intercept
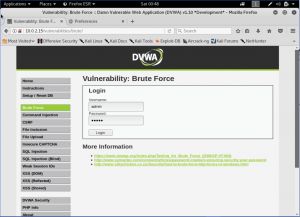
We then input any data to the username and password. After we input the data, we then go to the burp-suite to see how the request works.
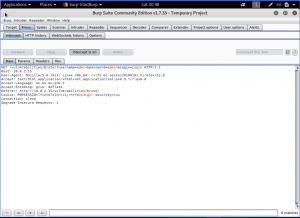
Now, after we intercept the request and find out how it works, we then send the request to the intruder (using Ctrl+I)
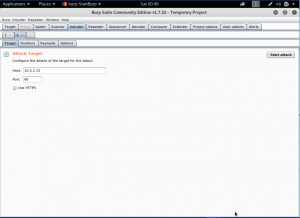
In the intruder, we will do some tweaks to make the brute-force attack works properly. First, we will set the payload positions into only the username and password area.
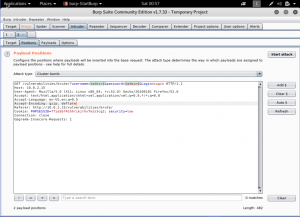
Then, we set the payloads data based on any possible username and password. There are many ways to do this. Some just fill it manually, some use the text file available on their system. In this case, i will fill it manually.
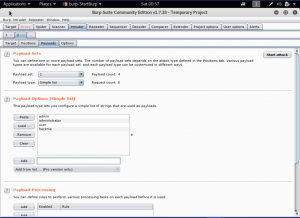
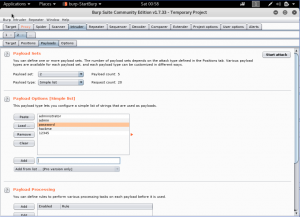
Lastly, we will fill the Grep-Match on options tab. We clear all the text there, and we add “welcome” What it does is to check if there is the word “welcome” in it.
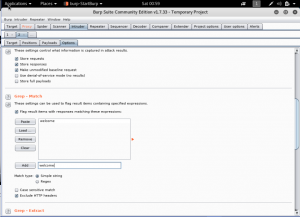
We then ready to start our attack. When we do the attack, we will shown the list of the username and password that we fill on the payloads area. And it will check if it the correct one or not.
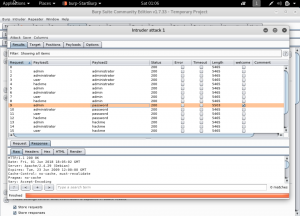
And we can see on the above, we already find our username and password. We know it because the welcome part is ticked. Means that there are the word welcome in it. Another sign is, it have a different length from the other. All that left is to input the username and password to the system. (Note: Make sure to turn of the intercept on burp-suite)
There is no difference on doing it whether on the low, medium or high level. It’s because we just need the request syntax and change the username and password payloads which are available on it. We use the low one to make it look simpler.
Brute-force attack could be one of the most simplest way to get into the system if we don’t prevent it. The way to prevent it is actually really simple. Just don’t use any easy password or passwords that related to you. Because the attacker must guess what are the possible passwords available to attack
