XSS (Cross-Site Scripting) Attack is a type of attack where a malicious script will be injected into a web server. XSS attack is usually happens when an attacker sending a malicious script to an unsuspecting user. XSS is used to get cookies, sessions, or maybe any sensitive information from users of the web application.
There are 2 types of XSS Attack: Stored and Reflected Attack. Stored Attack is where the script is permanently stored on the web servers, such as database, forums, comments, etc. The victim will then retrieves the script from the server when request the information.
The difference of Stored and Reflected Attack is not how it’s done, it’s more to where it’s done. If the input is sent and stored to the server or database, then it’s a stored attack. Which resulted to the script will be sent back every time the page is load and become “permanent”. While a reflected attack is happening on the input text that only able to read the database, such as search box. Which makes the reflected attack is not permanent, but still dangerous if not prevented carefully.
So, In this blog. we will learn how to make an XSS Stored attack and how we can prevent it.
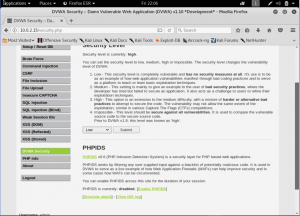
First, lets open the DVWA and set the security into low. And open the XSS (Stored)
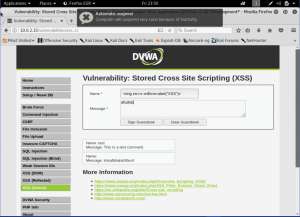
Now, lets just filled the data as it should be.
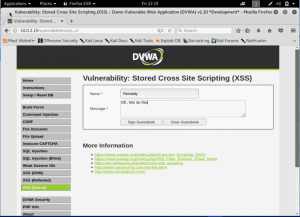
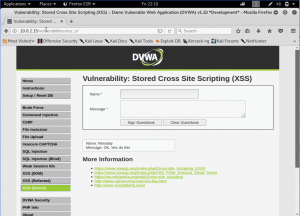
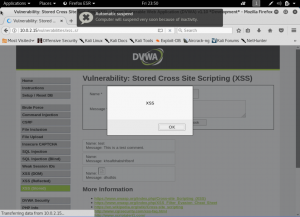
Here, the data is saved back on the database. As we can see that our input is being retrieved back. Now, let’s do our “hacking” by sending a simple malicious script to the page
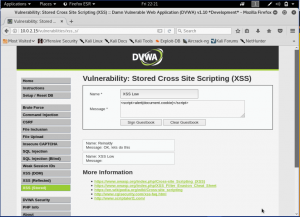
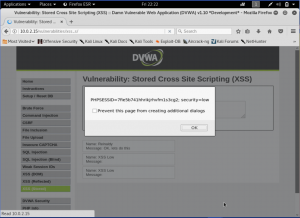
We can see that we have successfully gain the cookie of the page. Now, let’s see the source code to find out what’s really happening on the back.
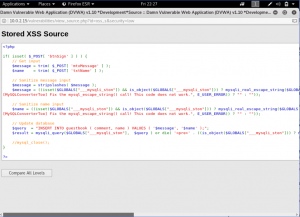
We can see from the source code, that in the message box, it only removes the backslash and escape any special characters. Which means that we can insert the script as usual.
Now, lets make the security to medium and once again do the attack as the above (Note: Reset the database again. Since it’s a stored attack, it will store the attack that we done before)
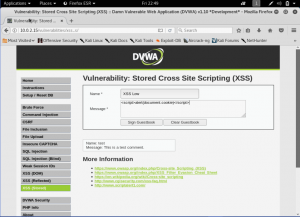
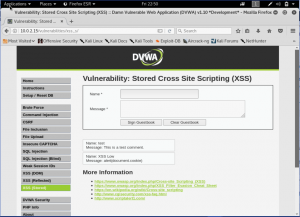
We can see here, that the attack is failed. There are no popup happening here, and the data is stored just like usual. Let’s see the source code to see what’s happening.
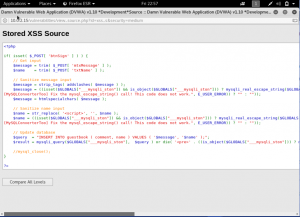
Here we can see that on the message input, the code will removing any tags and giving a backslash, resulting on the data is sent as usual to the database. While in the name area, we can see that the it only change the <script> into blank space.
The way to do this is to attack on the name box. This mean to have a uppercase/random-case letter of SCRIPT. But, we must also do something to the DOM if we want to do this type of attack. Because the page is stating that the max character is 10. We will delete it to make sure there are no limitations about how many character we input. Then we do the attack
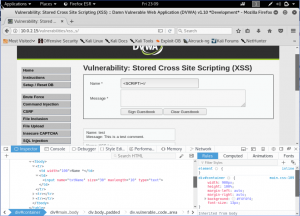
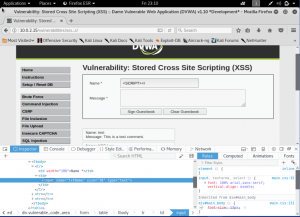
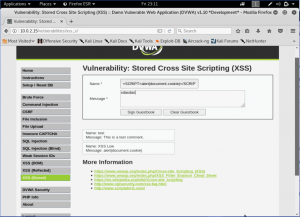
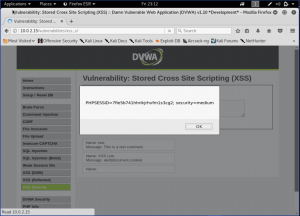
Now, let’s take it up a notch and make the security into high. Now, we will check the codes first then decide how to attack the page.
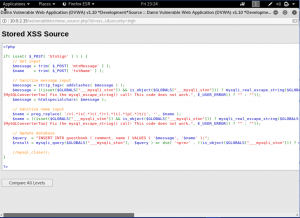
Here, we can see that on the name box, it uses a regular expression to find <script on the input. So the way to attack this type of security is not to use script tag. We will demonstrate 2 ways to do it. By using <body onload> and <img> tag. (Note: We will attack the name box. so we will change the maxCharacters every time we do the attack)
First, we will use the <body onload> tag. Means when we load the page, it will show what it done on the tag.
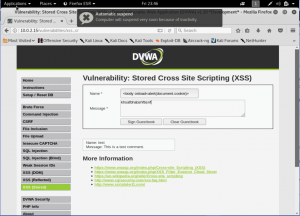
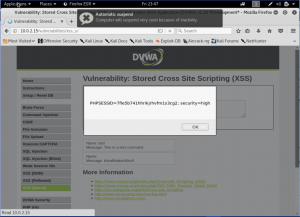
Another way is to use the <img> tag. Well, it’s normally used for an image. But, we will purposely sending no image and we will put a ode that said if there are no image, then do this thing (In this case a popup).