XSS (Cross-Site Scripting) Attack is a type of attack where a malicious script will be injected into a web server. XSS attack is usually happens when an attacker sending a malicious script to an unsuspecting user. XSS is used to get cookies, sessions, or maybe any sensitive information from users of the web application.
There are 2 types of XSS Attack: Stored and Reflected Attack. Reflected XSS is where the injected script is reflected of the web server. Such as in an error message, search result, or any other response that includes some or all of the input sent to the server as part of the request. Reflected attacks are delivered to victims via another route, such as in an e-mail message, or on some other web site. When a user is tricked into clicking on a malicious link, submitting a specially crafted form, or even just browsing to a malicious site, the injected code travels to the vulnerable web site, which reflects the attack back to the user’s browser. The browser then executes the code because it came from a “trusted” server.
Stored Attack is where the script is permanently stored on the web servers, such as database, forums, comments, etc. The victim will then retrieves the script from the server when request the information.
So, our goal here is to learn how to do the XSS Reflected Attack and how to prevent it to happen in case we want to create a web application. (XSS Stored Attack will be done in the next blog.)
- Reflected XSS
So first, let’s open the DVWA that we already installed on before, and set the security to low.
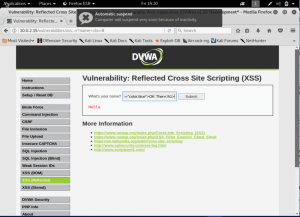
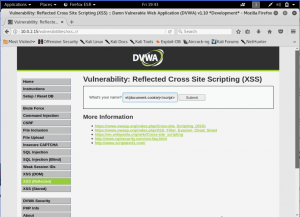
We then go to the Reflected XSS Tab. Let’s just fill our name first then.
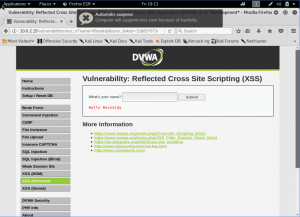
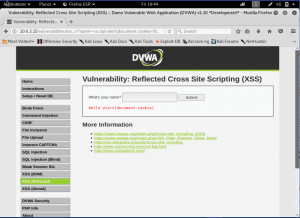
Well, we can see our name is displayed below. Let’s start do some “hacking”. Inject a simple code to alert the cookie of the page.
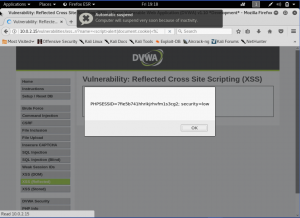
We can see the cookie of the website. Now, we will look on the source code how could it be happening.
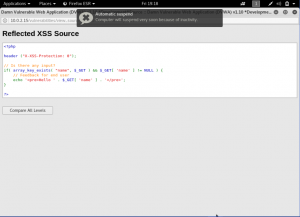
We can see, the input box is just taking the input as it is, meaning they wouldn’t change anything that is inputted. Resulted on a simple malicious script is able to be send. We can now “fooling” a little then now that we understand the source code. Let’s just change the HTML Interface. Let’s make the output to be a header and blue in color.
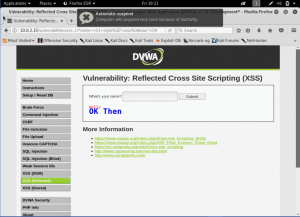
There, because it doesn’t change anything n the input box, we can even change the interface of the web application. Now let’s take it up the notch and make the security into medium. and lets do another XSS Attack.
Let’s insert a script as usual. just as what we do on the low level.
We can see here that the result is not the same as before. It wouldn’t make an alert, instead, it will sent a as you can see above. Now, lets see the reason by looking at the source code.
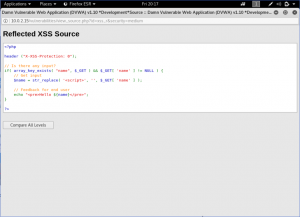
We can see from the source code that if we input an usual script. It will change the <script> tag with a blank space. We can pick one of the 2 most easiest way to penetrate it. One is by making the script tag into uppercase or random it between uppercase and lowercase. Remember that HTML Tag is not case-sensitive. Meaning we could just change the script tag into SCRIPT.
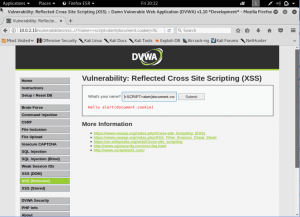
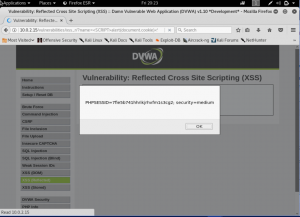
Second is by using <body onload = alert(‘XSS’);> This is a usual script that works the same with the usual, but instead using script tag, it will asked when the page is loaded, it will alert the XSS
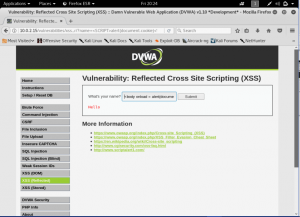
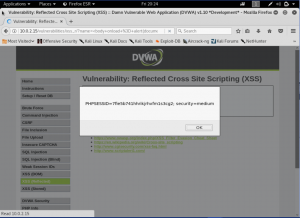
Next, lets take it up a notch again and make the security level into high. And let’s see to the source code of XSS (Reflected) on level high.
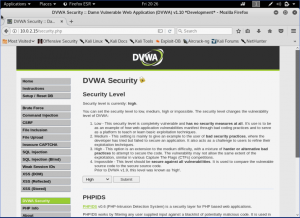
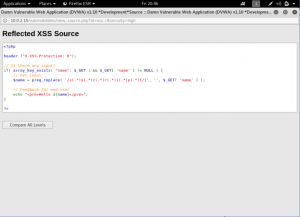
We can see from the source code, that it uses regular expression to remove any <script from the input. Meaning, we couldn’t use any script tag from before. But, we still can use the body onload tag to do the XSS Attack. let’s try it then.
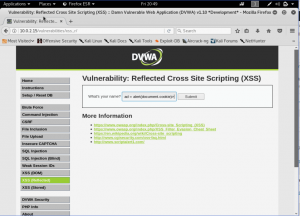
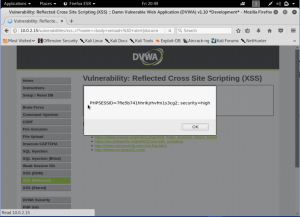
Another way to do it is by using an <img> tag. Well, it’s normally used for images, but if we put onerror to do the popup. It will work the same with the above. The reason is there are no pictures uploaded. Meaning, if the picture is unable to be uploaded or error, it will trigger what’s inside the onerror.
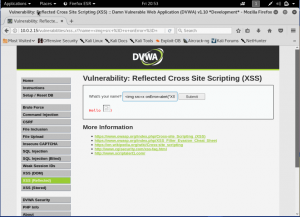
Obviously, XSS Attack could be dangerous, it could disturb the user experience, take the session of a logged in user, or even take any sensitive data from users. There are ways to prevent XSS attack to be happened. By Escaping and Sanitizing user input and also by Validate user input. Escaping and sanitizing means to taking the data and make sure it’s secure before render. Validating is to check the user input if there are anything that could be used to attack.
References:
https://www.owasp.org/index.php/Cross-site_Scripting_(XSS)
