After we gather data about our target. We can search and find our target. Here, the tools we use will be dnstrails.com, robtex.com and also crimeflare.org
- dnstrails.com
dnstrails.com is a website used to find out and data regarding about our target’s website.
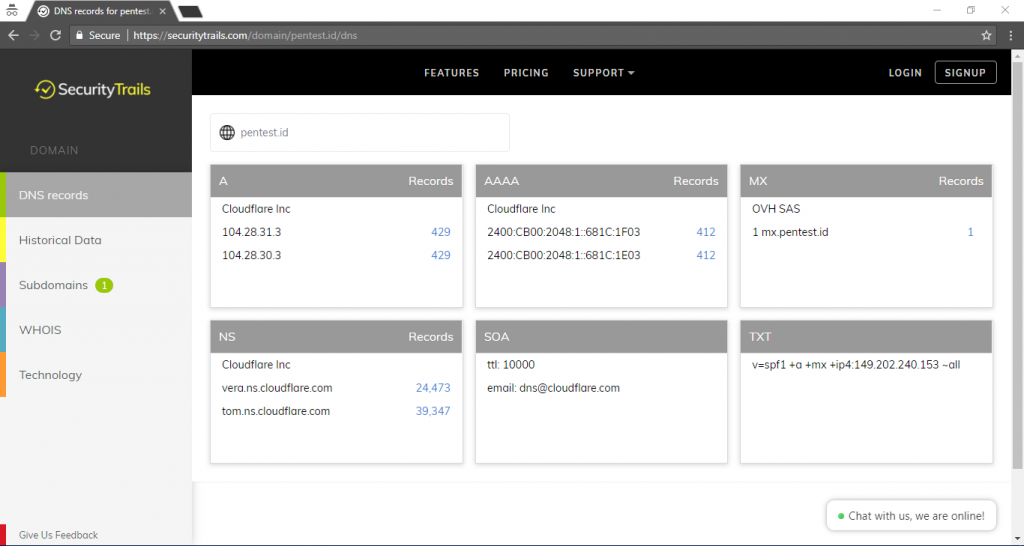
in the example above, we can search and see everything about our target’s website (In this case pentest.id). We can see their IP4 Address (A), IP6 Address (AAAA), Mail Services (MX), Name Server (NS), Start of Authority (SOA), and also Text file (TXT).
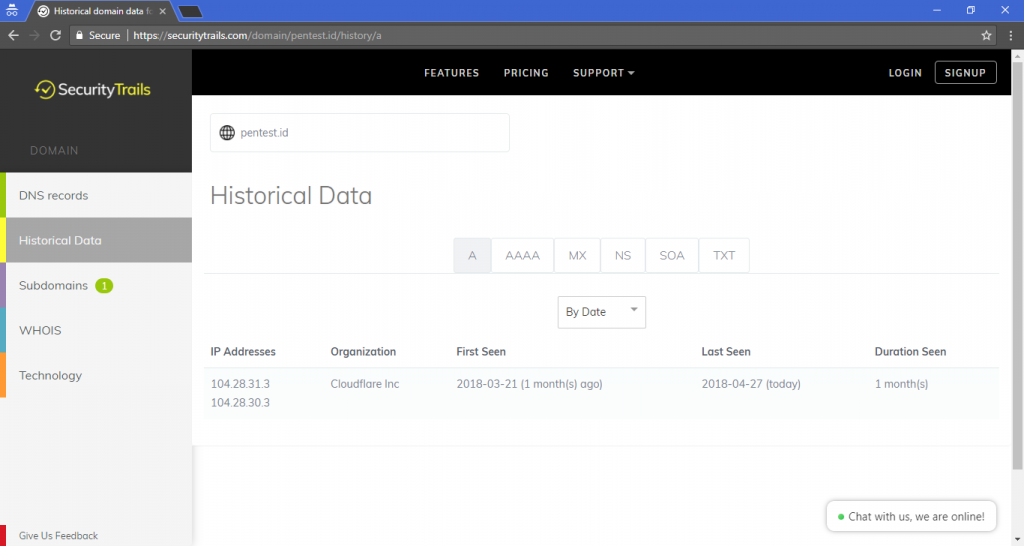
We an also see the history of the target’s website. Their website history could tell us a lot of things regarding about their website and probably their company.
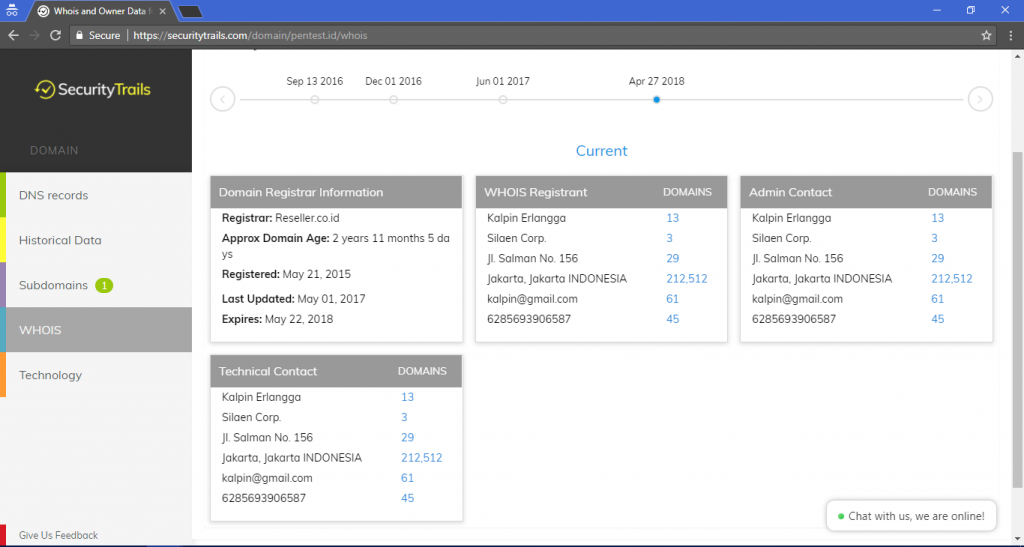
We can also search about the website registrant’s name here. This could important because we can know about the registrant data.
2. robtex.com
robtex.com is another website used to find user’s data from their website
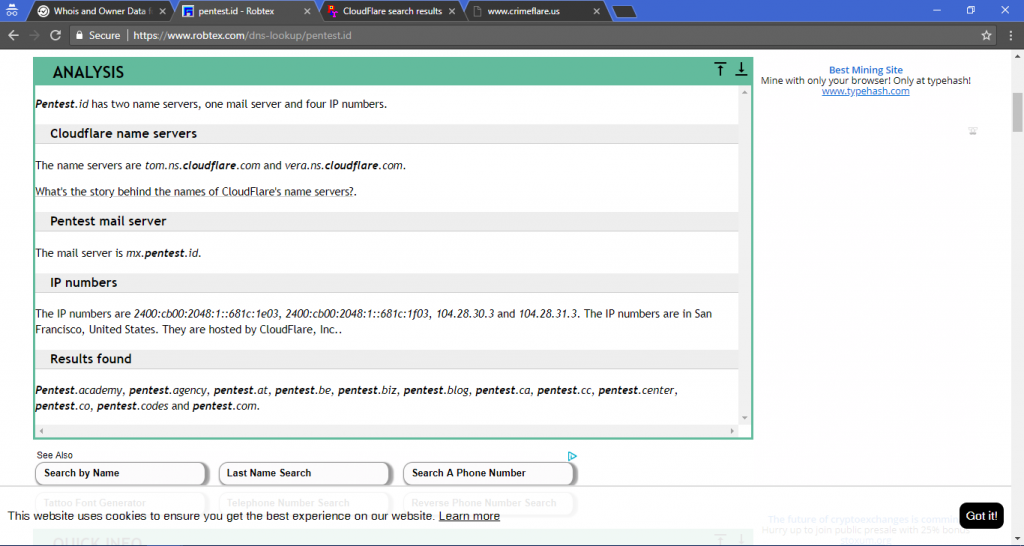
Here, we can see about some analysis of the website, info about the website, records, SEO and many more about our target’s website.
We can see here that those website are using cloudfare servers. Cloudflare, Inc. is a U.S. company that provides a content delivery network, DDoS mitigation, Internet security services and distributed domain name server services, sitting between the visitor and the Cloudflare user’s hosting provider, acting as a reverse proxy for websites.
Reverse proxy for websites means that a website have 2 IPs. One is their real IP and another one is an IP that’s covered by cloudflare. Which means, if we don’t know their real IP. We couldn’t launch an attack to our target website.
One of the tools used to know one’s real IPs is by using crimeflare.org. crimeflare.org is used to know one’s real IP behind their covered IP.
Another way is by looking at their website history. This is where the historic data of a website become important. Since cloudflare is only covering the real IP, It’s possible that that the IP for the website is still the same as the one used to. It just they used cloudflare services to do reverse proxy and make their real IP’s covered
