Port Scanning is a way to find out which service are offered by a host. Port scanning is able to identifies vulnerabilities. Port scanning can be really useful, because port scanning are able to find any open services available and found any vulnerable port, which we could launch our exploit from.
There are 7 known types of port scanning
- SYN Scan -> Stealthy scan
- Connect Scan -> completes the 3-way handshake
- NULL Scan -> packet flags are turned off
- XMAS Scan -> FIN, PSH, URG flags are set on (Feels like Christmas Presents!!!!)
- ACK Scan -> Sending ACK Flag, Used to past a firewall
- FIN Scan -> Send FIN Flag, Closed port will respond with RST flag
- UDP Scan -> Closed port will respond with ICMP “Port Unreachable” message
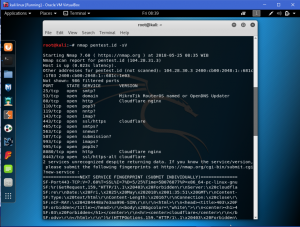
One of the most famous tool to do port scanning is called nmap. Nmap (Network Mapper) is a security scanner used to discover hosts and services on a computer network.
The most simplest command that usually used on nmap is
nmap *IP Address/Domain name* -> used to scan a single website / IP Address
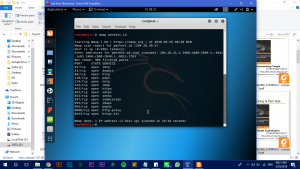
nmap *IP-Add IP-Add* -> used to scan more than 1 IP Address
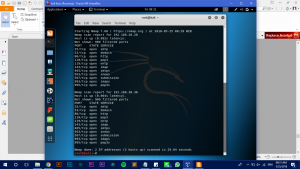
Those 2 scanning type is by default a SYN Scan. We can specify the type of scan that we would like to use.
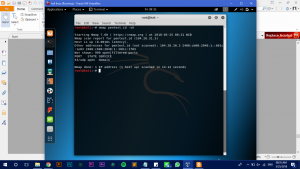
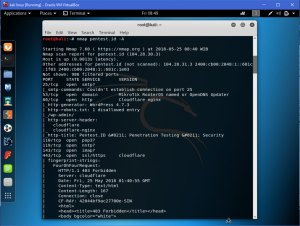
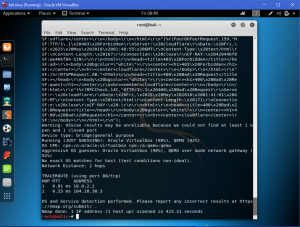
We also could check for the website version and to give all data about the website