Social Engineering is really important on doing penetration testing. Especially, if one is doing it using black-box model. The reason is simple. Because person keeps making mistakes. A person could make mistakes without they realize.
The goal of social engineering is to obtain any important and/or confidential information through human communication. There are 2 common tactics on doing social engineering: Interview and Interrogation. Both of the tactics are done on relation of “trust, meaning the person we want to get data from must “believe” in us before we can get any important data from them.
The process of doing social engineering are:
- Intelligence gathering
- Identifying any vulnerable points
- Planning how to attack the vulnerable points
- Execution
There are also a lot of methods that could be done to gain information. The most known one are:
- By impersonating a person (Usually done not face-to-face)
- Reciprocation (exchange favors in terms of getting mutual advantage)
- Influential Authority (Becoming a “figure of authority”)
- Scarcity (Make the person have no other option but to give you the information by scaring them)
- Social Relationship (By making a relationship to the target)
But, there are more ways than the above to find important data about the target. We could do it by peeking through their phone, looking at their web history, or just looking through the files could help you find any important data about the target
There are some tools known to do social engineering. Here, I would explain using SET (Social Engineering Toolkit) to gain information from user of a website. Basically, it’s copying another website to our IP Address to gain information about the target.
We start by typing ‘setoolkit’ on the terminal
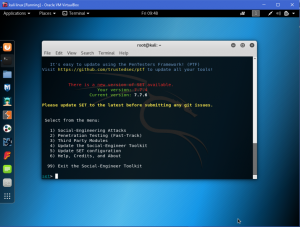
Type ‘1’ for Social Engineering Attacks
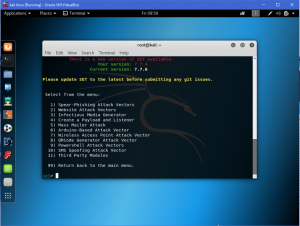
Type ‘2’ for website attack vectors
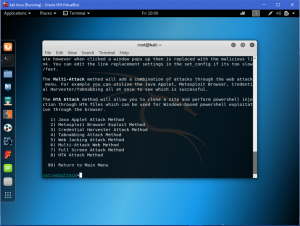
Type ‘3’ for Credential Harvester Attack
Type ‘2’ for Site Cloner
Insert the IP Address where the website will be copied (In this case, we would use Kali IP. But, it’s also possible to use an external IP)
Insert the copied website (in this case, we will copy facebook.com. But, we may use any other website that have login access)
Now, open the IP that we just copied the website. And, we will see the copy of the website. Let’s see how does the information is taken from it. So we insert our ‘data’ inside and look at the terminal what will happen inside the terminal.
In the terminal, we can see the user data that we just input inside. Imagine how many data we could take if we share the website to others. This is called phising, where we gaining any credentials information from an user without their permission.
We could prevent being the victim of phising by simply taking time to carefully look around the website. First, we can see that the domain name is wrong. It will be different from the real website. Second of all, after we input our file, it will once again show the login page of the real website (But, this one means they probably have our data).
