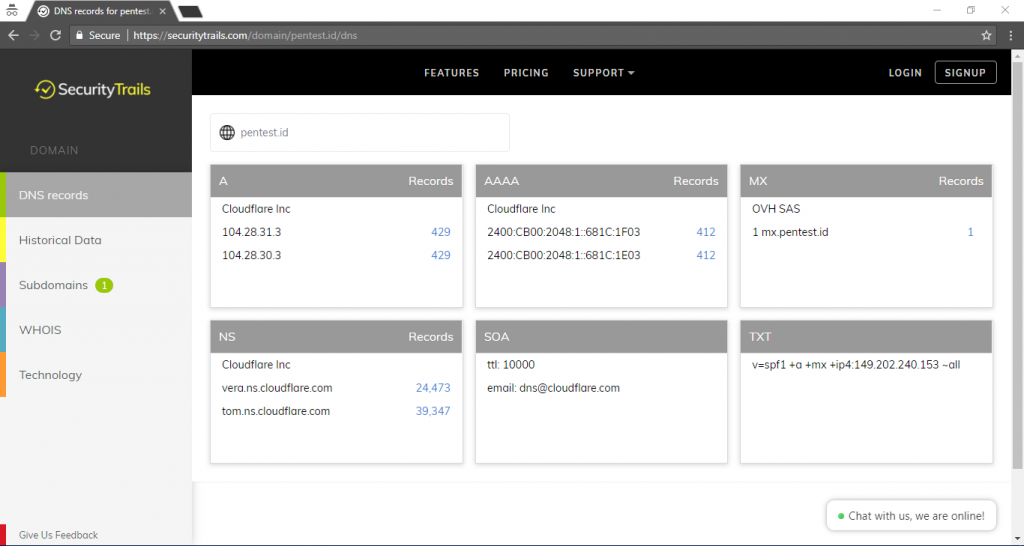
CREATED BY:
Reinaldy Edbert Fargo (2001594573)
R. Aditya Pribadi K.
Background
We are asked to create a game for a kindergarten students for the final projects. So, we created a game called “The Adventure of Timmy”. “Adventure of Timmy” is actually called a journey-type of game rather than a usual game. Since kindergarten students are just not really learning and just want to playing games. We created the games into a journey to safe animals and pets. It’s basically because it’s actually a mixture of 4 game created for kindergarten students that help them improving their skills which are math, shapes knowledge, words and also a fun maze in order to make kindergarten students feel happy to play.
Description
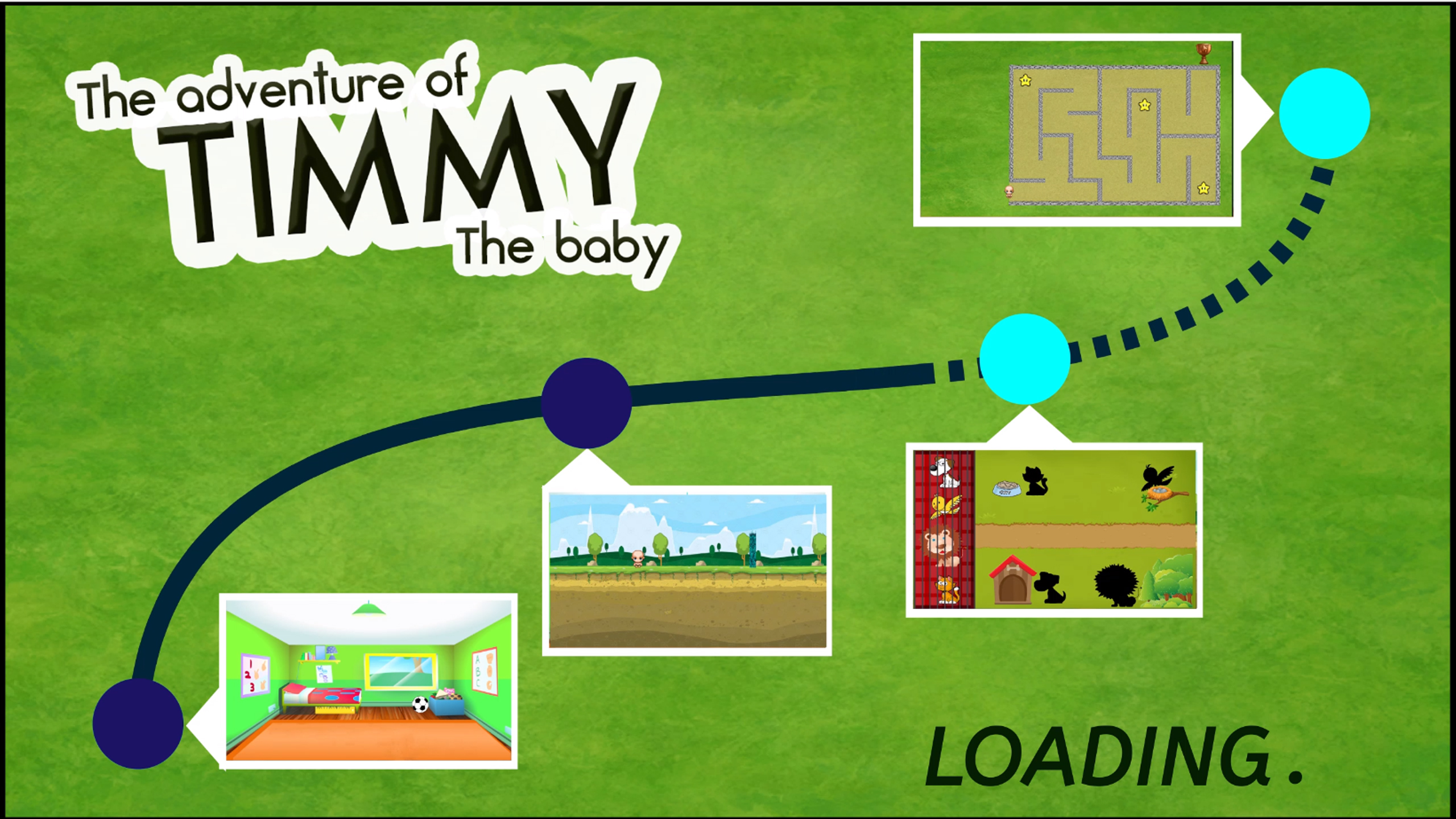
We created 4 games to create a journey inside the games or kindergarten students. Each games is started by a video of the maps to help the player to remember which stage they already in and what type of interface they will have. The games is also started an ended with a dialog by Timmy to help the player’s to understand the task and also to make the game to be a unity and a journey. Each games is also have the help button to help the player to understand the way to play the game.

1st game
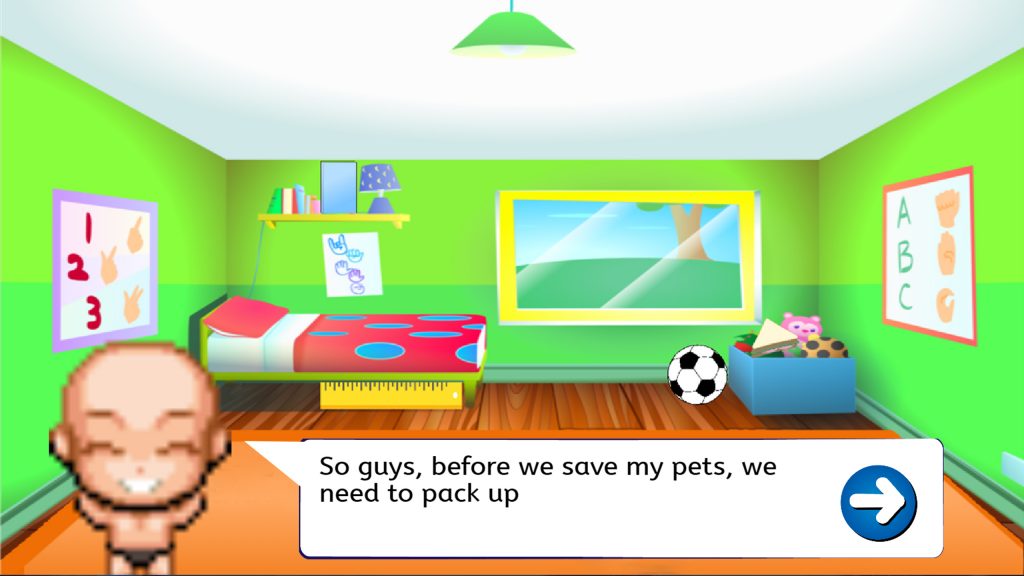
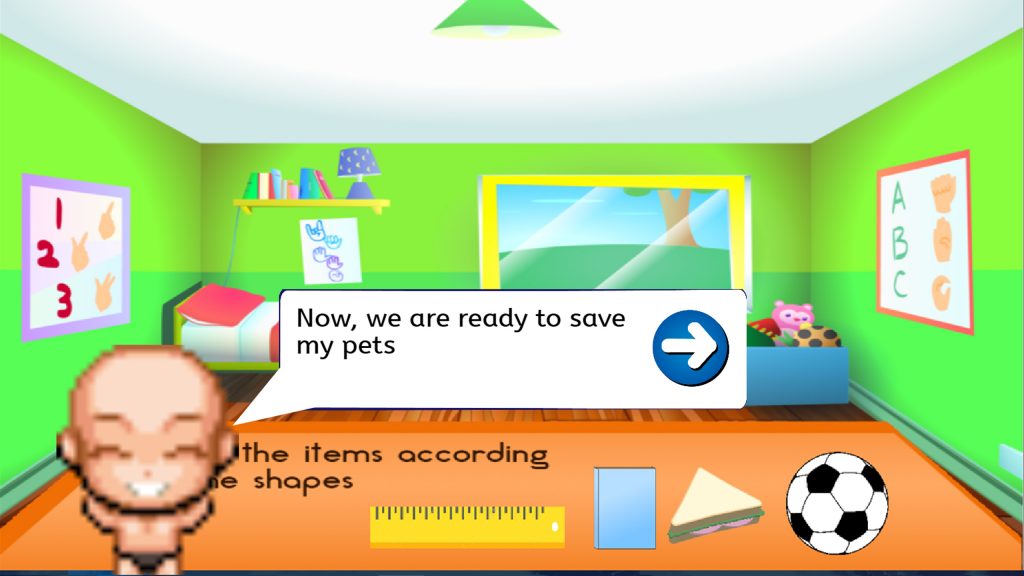
Before “Timmy” is getting out saving his pets. He must pack his stuff first. In this games, children will learn about shapes. They must find things that have similar shapes as the shadows shown on the game. In this game, there will be a help button to help the player understand the game.
To be more specific, the things are scattered around the room and that is the player’s job to find the object and to drag it to the right place according to the shadow’s shape. Here, the player’s way to play is by dragging the things inside the room. After the player already did the job, they are ready to start their adventure.
2nd game
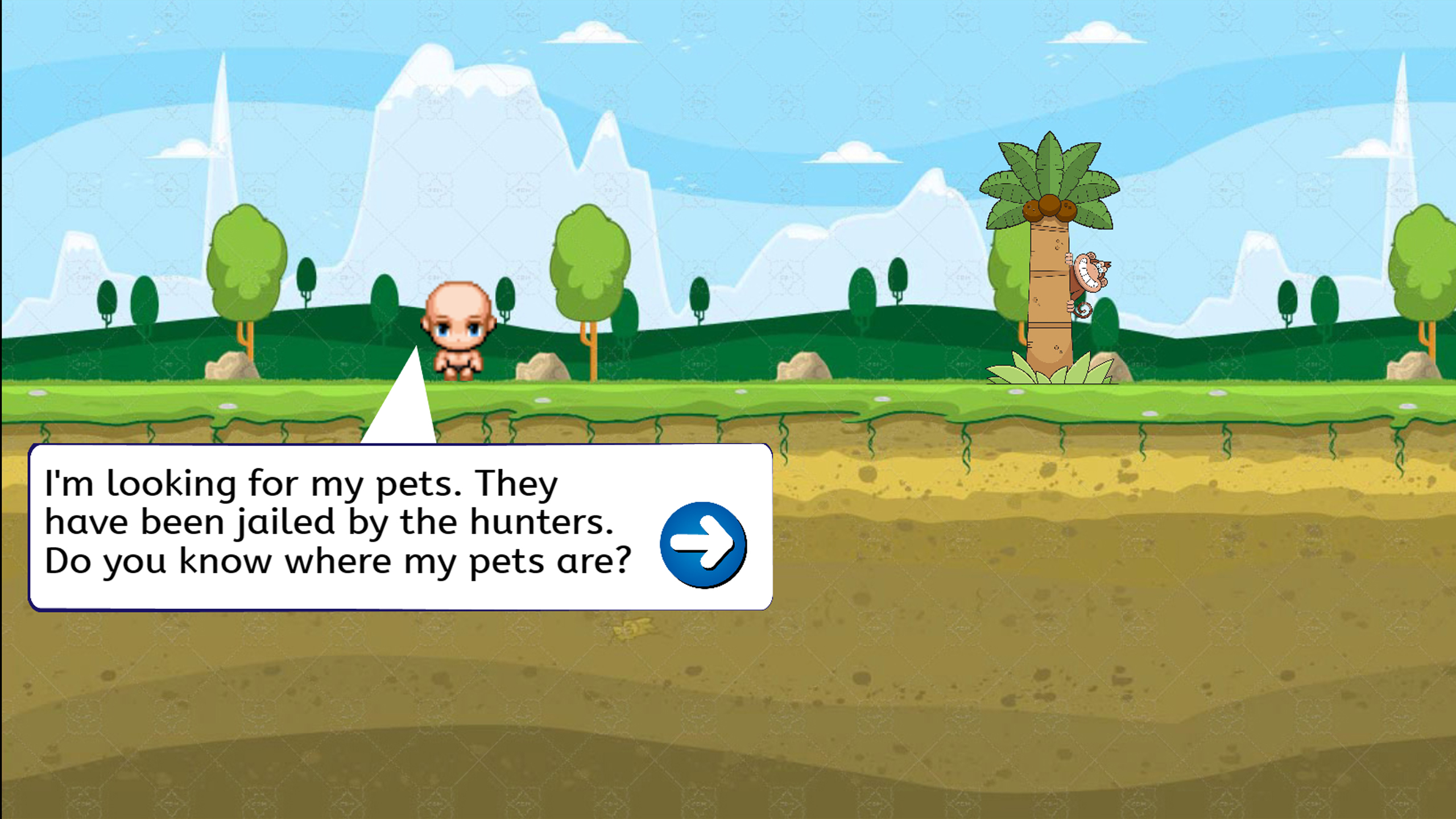
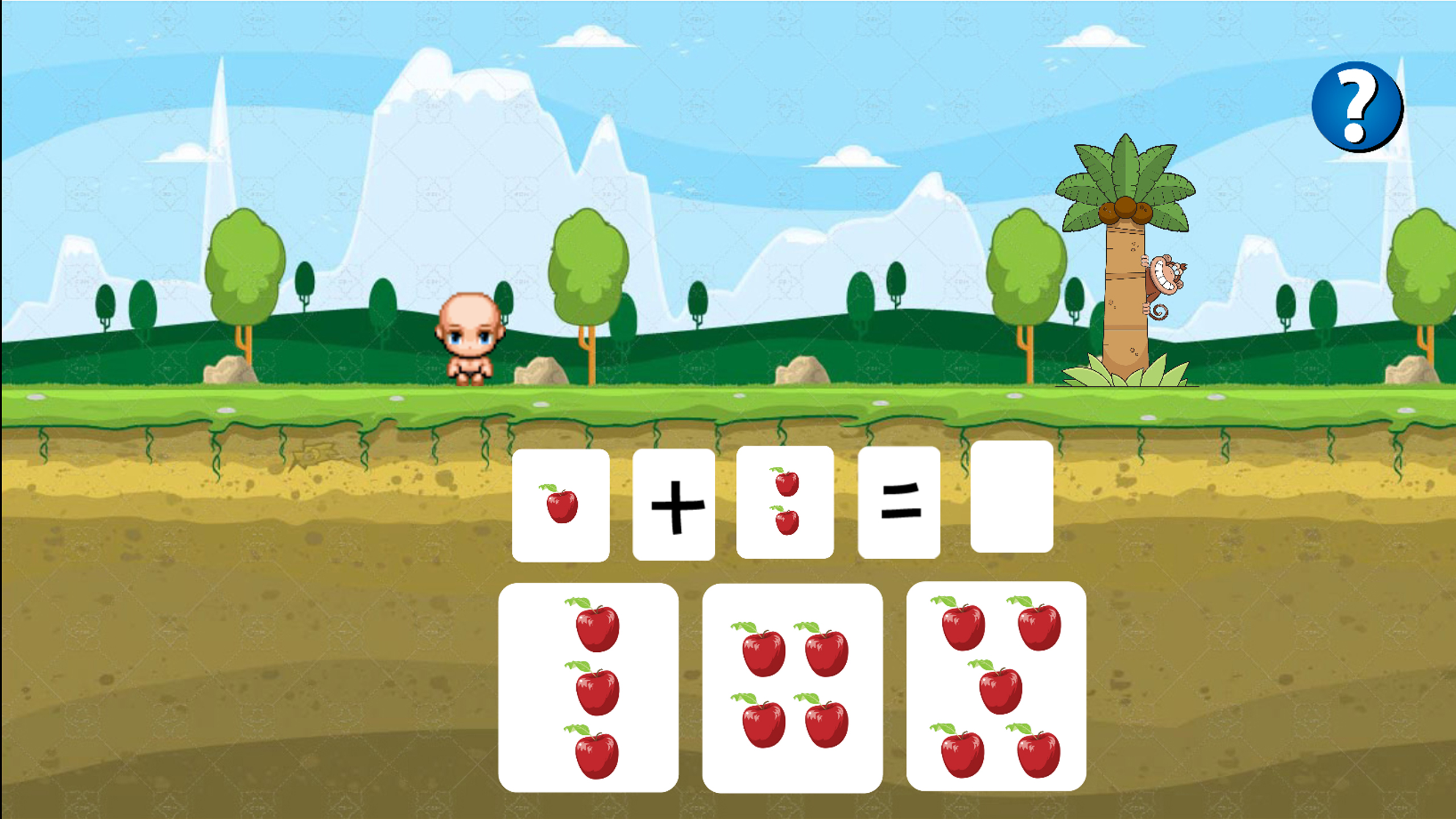
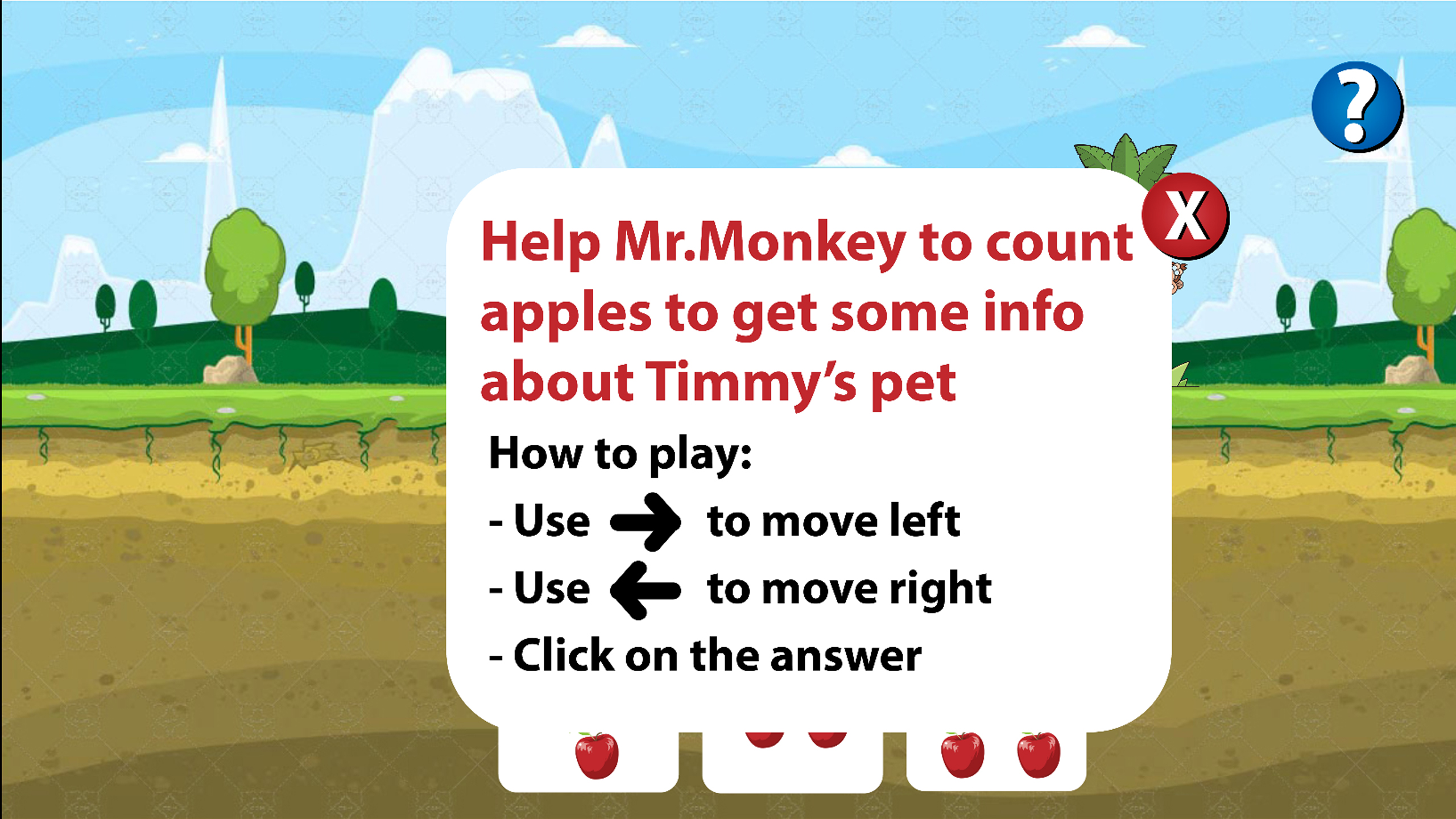
Now, Timmy is on a journey. He sees Mr. Monkey on the tree. Timmy then asked Mr. Monkey if he knows where his pets are. Mr. Monkey said that they have been captured by the hunters and knows where his pets are. But before that, Mr. Monkey ask Timmy to help him counting the amount of apples.
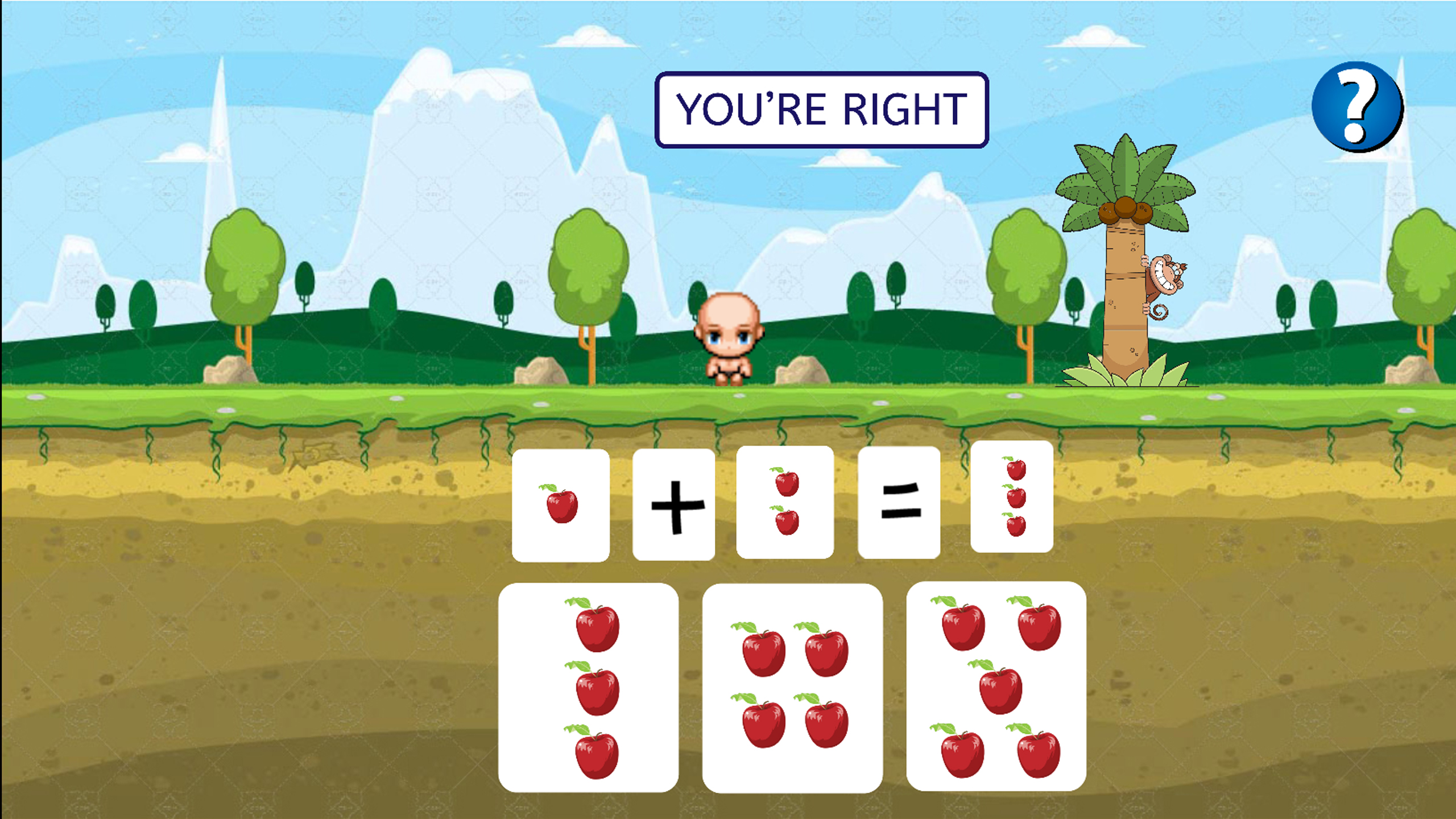
The player will be shown a math question and 3 answers. The question will be all addition question. The question and answers numbers are shown as apples. Since it’s better for them to understand and count via picture. The player’s way is to click on the right answer. Then they will be given 2 more question to answer. Total will be 3 questions with different level. They will be shown if they haven’t choose the answer or pick the wrong answer. The player’s control will be by using left arrow and right arrow, also left click to choose the answer.
After they answer the 3rd question. They will be shown the monkey and will be told that the pets are caged and then Timmy continue his adventure.
3rd game
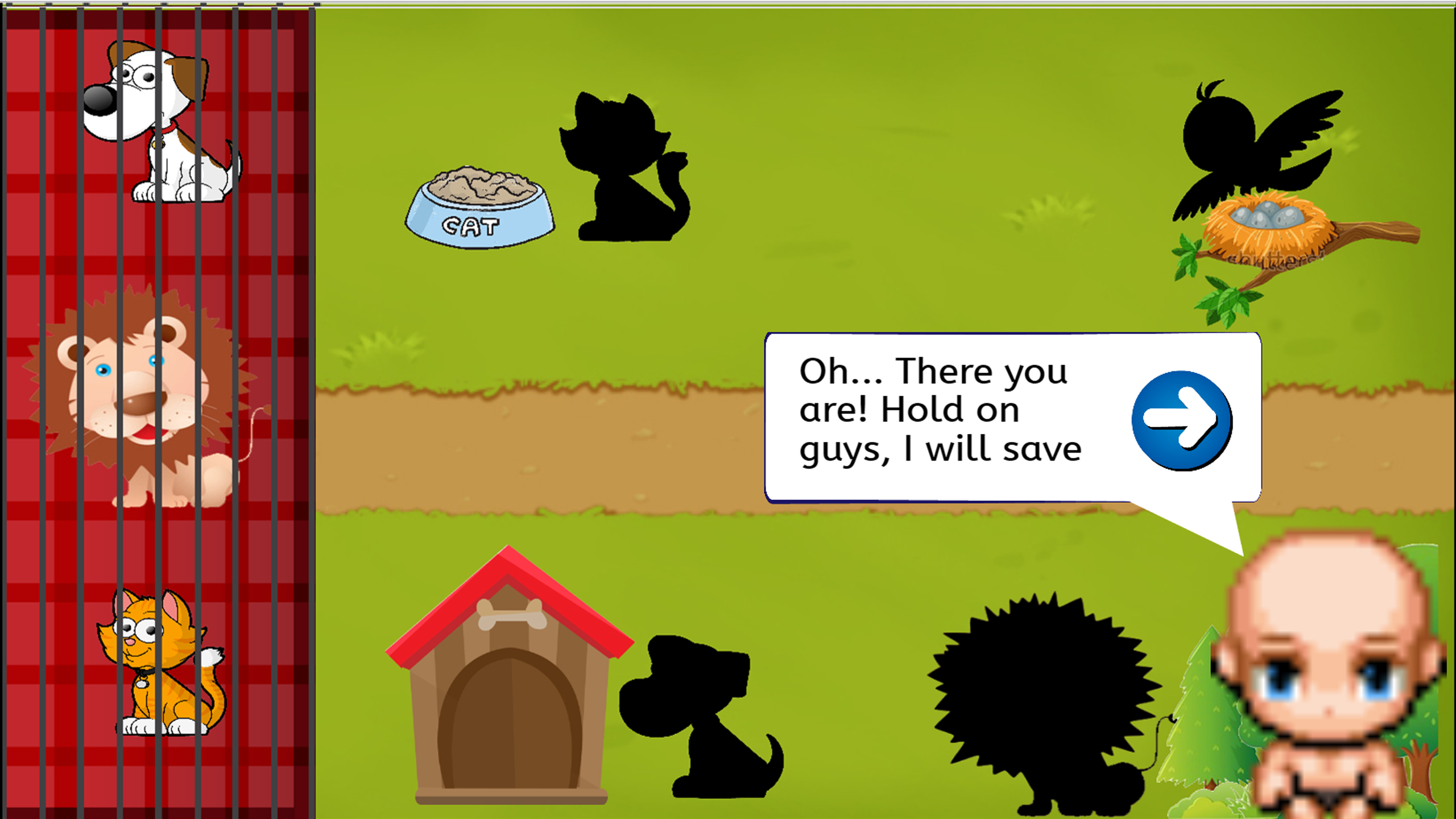
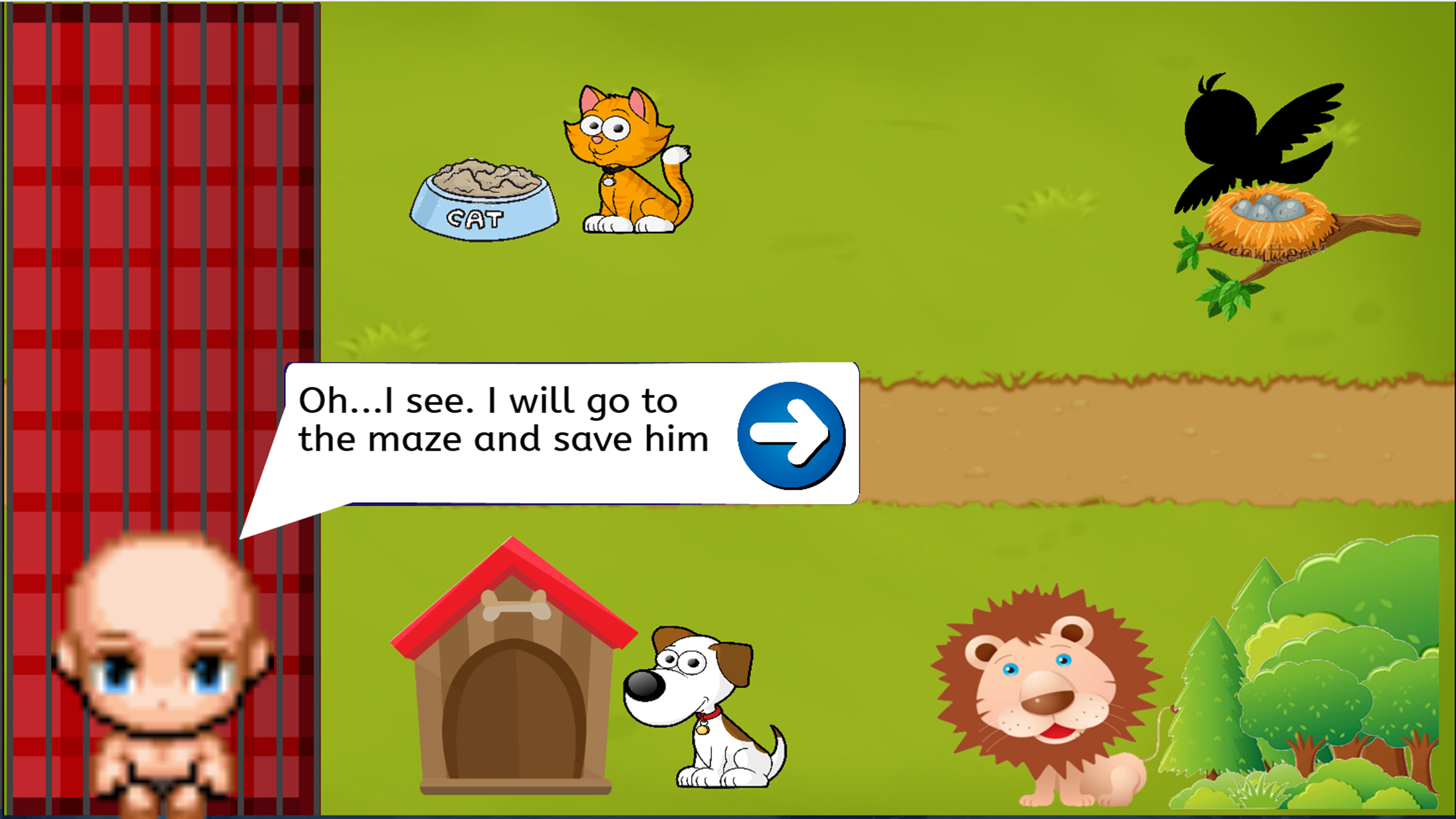
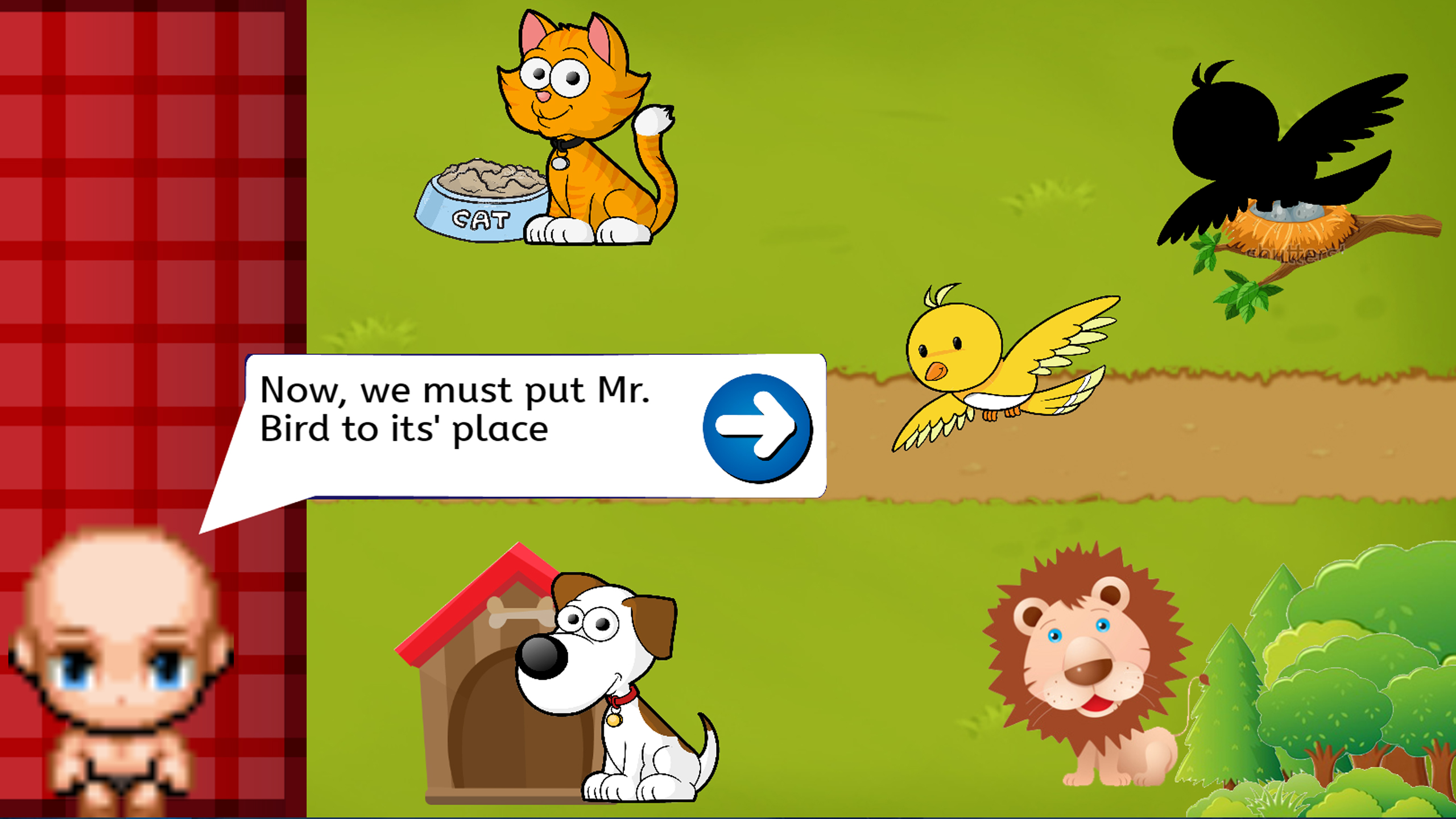
Timmy then sees his pets inside the cage. He must save his pets by putting the animals according to their living places. He then found out that Mr. Bird is not inside the cage. He then told that Mr. Bird is inside the maze. Timmy then go to the maze.
The player’s control will be the same as the 1st game where the player must dragged the animal according to the animal shape and their usual living place. It’s intentional not to put the bird, because in the next game they have to save the bird from the cage and later will put the bird back to it’s place
4th game
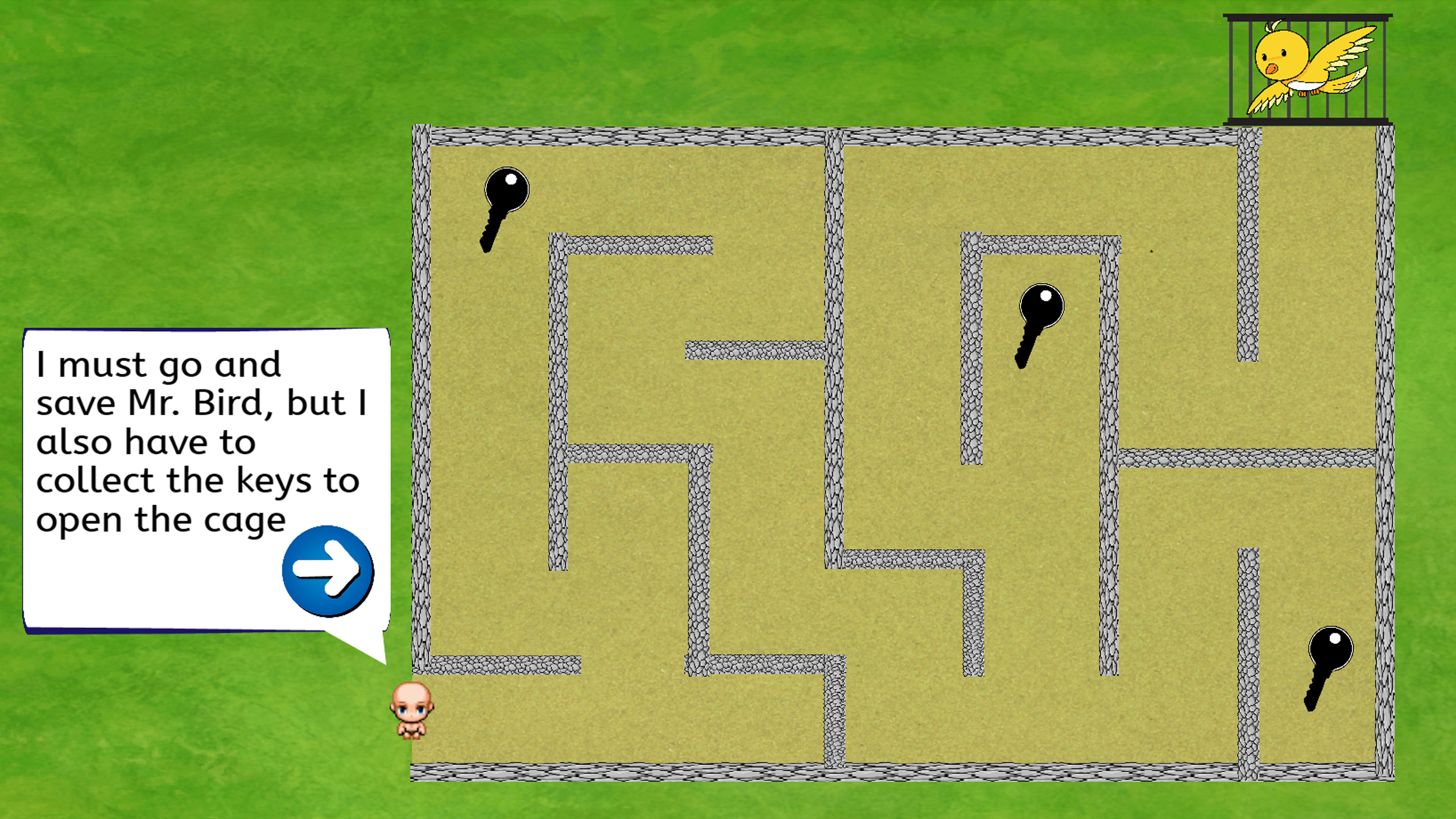
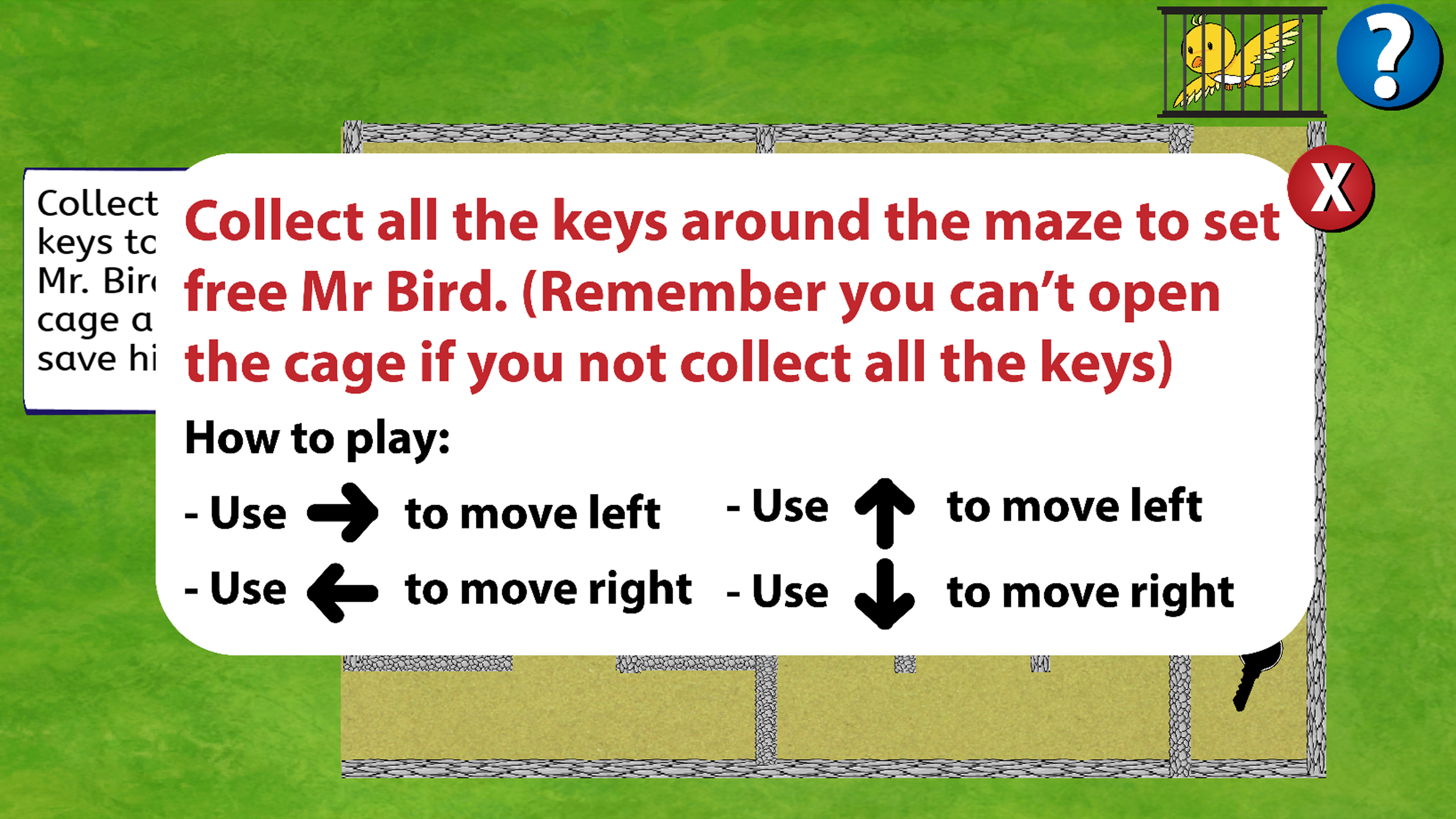
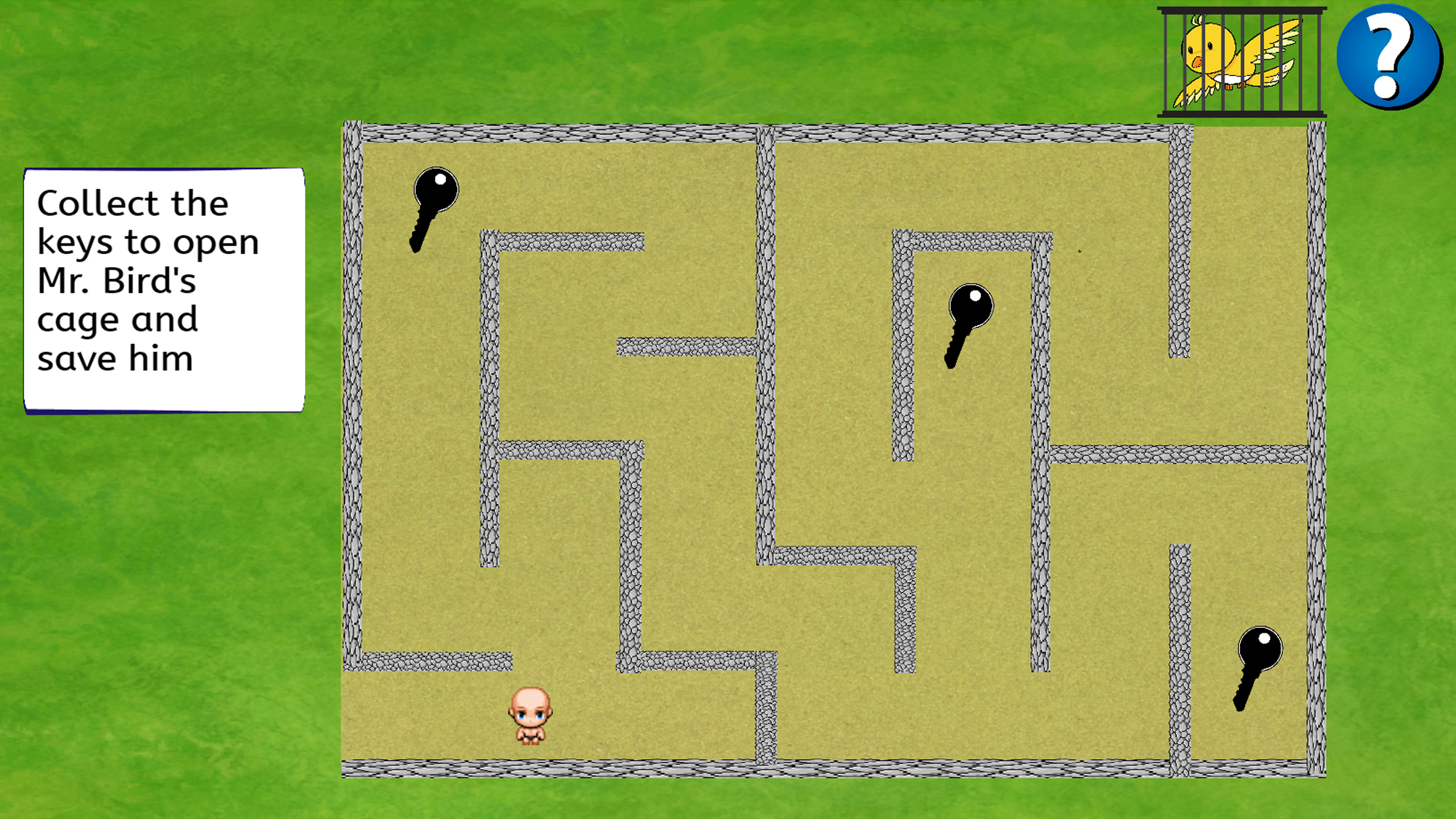
Timmy is already in front of the maze. He sees Mr. Bird inside a cage. But, before he could save Mr.Bird, he must collect 3 keys to open the cage. After he collect the 3 keys, the cage will be opened and the player must go to the bird to save the bird.
The player’s control will be only the arrows button. Meaning they only need to use the left, right, up and down button to play the game which is similar to a RPG type of game.
After Timmy save the bird, they will back to the 3rd game where he need to put the bird to it’s place.
5th game (4.5th game)
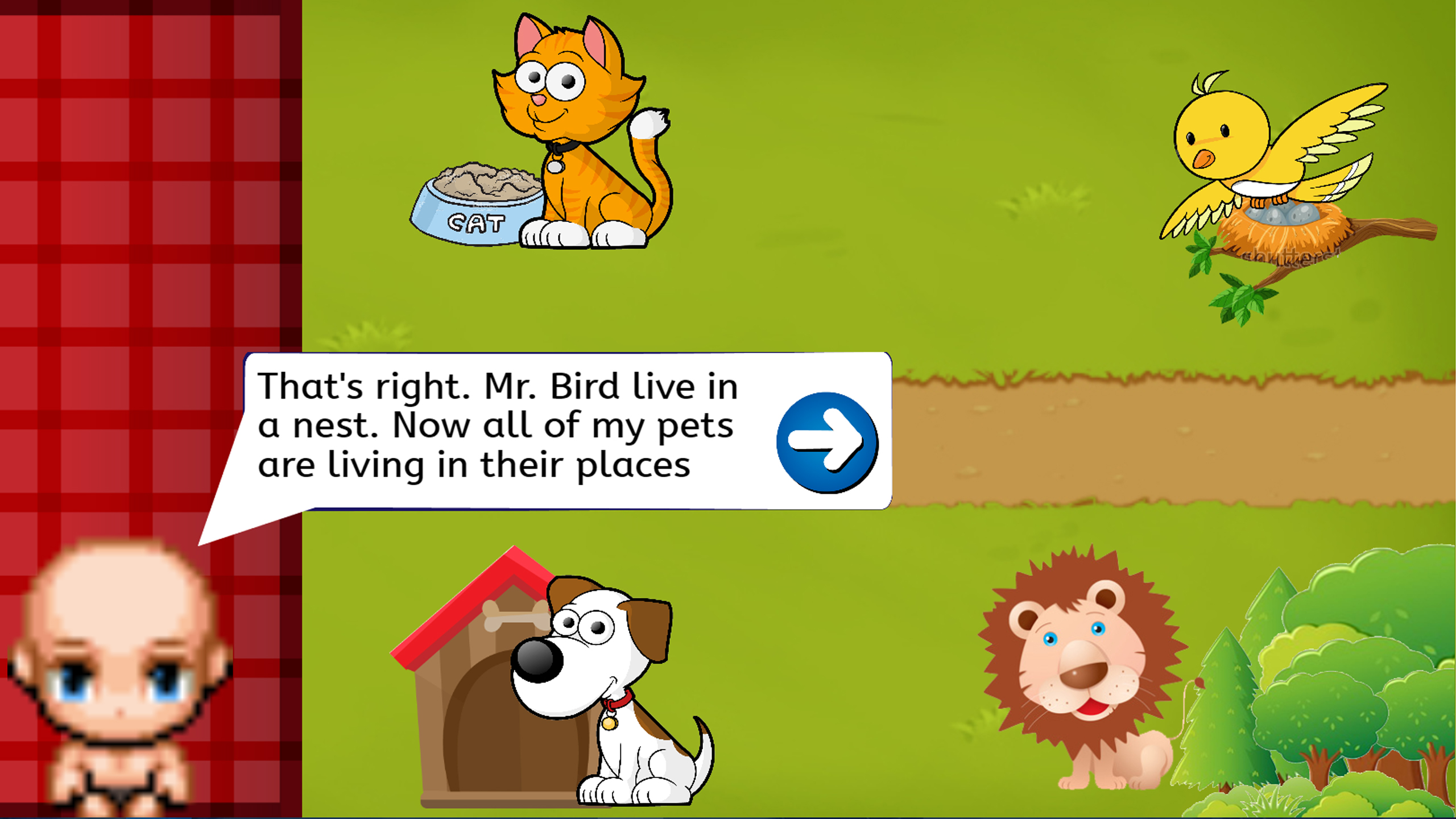
Timmy already save Mr. Bird, he then comes back to the 3rd game to put the bird back to the nest. Mission complete.
The player’s way to put the bird back to it’s place is to drag the bird to it’s place, which is the nest. After the player put the bird back to it’s nest. The player will tell that the mission is a success and say Thank you. Then they will back to the start page
-The game end-
Credits:
Kids : https://forums.rpgmakerweb.com/index.php?threads/base-sprites-emotes-and-animations.56332/
Picture sunrise: http://pictures-and-images.net/single/67_wallpapers-others-create_3.html
Room: https://yuzikoi.deviantart.com/art/Kids-room-background-213138025
Ball: http://clipart-library.com/vector-soccer-ball.html
Sandwich: https://es.vecteezy.com/imagenes-vectoriales-comida/94117-vector-de-club-sandwich
Ruler: https://www.123rf.com/photo_53409373_stock-vector-ruler-flat-icon-vector-illustration-ruler-icon-school-icon-symbol-ruler-education-equipment-some-yel.html
Book: http://www.clker.com/clipart-blue-book-1.html
Grass backgorund: https://gameblox.org/editor/16988/
Monkey on tree: https://www.istockphoto.com/vector/cartoon-monkey-tree-gm531777215-55523992
background part 2: https://www.gamedevmarket.net/asset/animals-sprite-sheet-and-one-background-with-multiple-possibilities-2052/
Apple : http://karlmac.com/2011/10/apple-vector-art-free-download/
Lion : https://pngtree.com/freepng/lion_2437454.html
Bird : https://www.123rf.com/photo_2019435_cute-bird-vector-illustration.html
Cat : https://www.jamiesale-cartoonist.com/free-cartoon-cat-vector-clip-art/
Dog : http://animalia-life.club/other/dog-vector-png.html
Cat food : https://www.istockphoto.com/vector/cat-food-bowl-gm510332510-84042403
Dog house : https://www.clipartsgram.com/download/AeBZz2O
Trees tiger : https://www.freepik.com/free-vector/coloured-trees-collection_1021178.htm
Bird nest : https://www.shutterstock.com/image-vector/four-eggs-bird-nest-illustration-471817127
Key : https://www.clker.com/clipart-key.html
Rock : https://play.google.com/store/apps/details id=appinventor.ai_SidhKulkarni1.PetRock