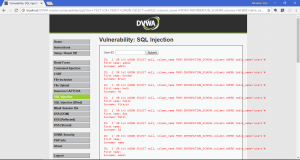
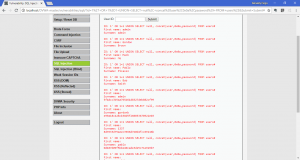
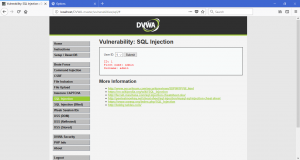
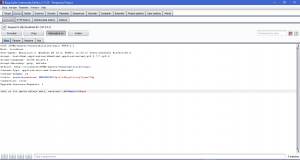
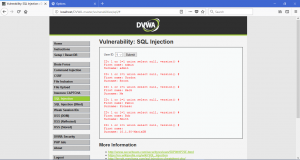
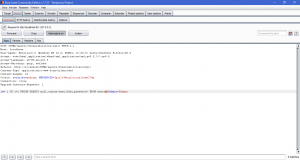
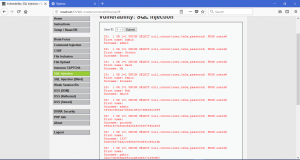
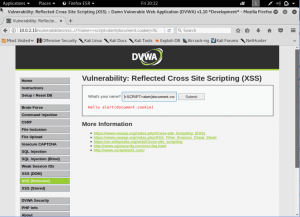
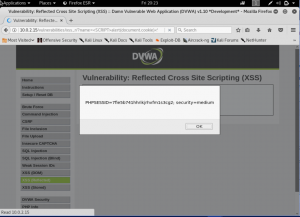
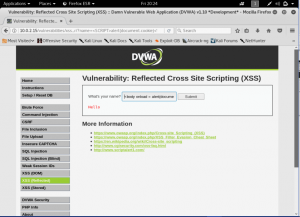
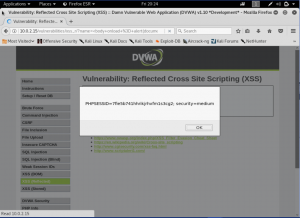
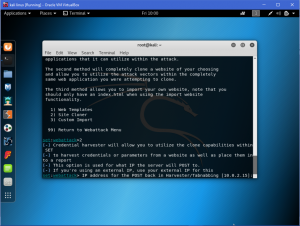
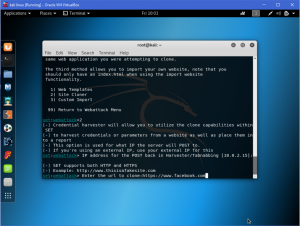
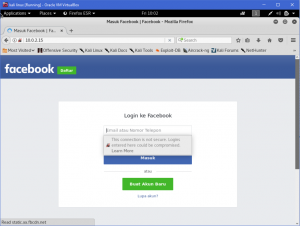
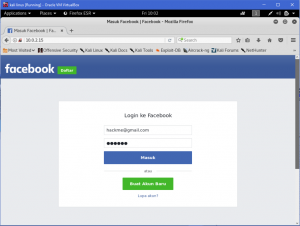
What is network forensics? It seems that hearing the word ‘network forensics’ will make us think that it would be really cool and in the same time difficult. So what is this ‘network forensics’ to be exact?
Basically, Network forensics is a part of digital forensics with focus to monitor and analyze network traffic. Network forensics is usually used when there’s an intrusion detection/prevention, information gathering and legal evidence.
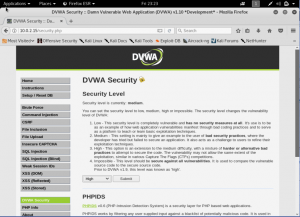
Although sound similar, network security and network forensics are two different thing. Network security is used against an attack which happen real time and works 24h. you can think as a security personnel in front of a bank. While in network forensics, there are no protection against system attack, happens after the incident happened and after the crime happened . You can think as a detective who works after an incident happens or a case is found.
So, why network forensics is really important? Network forensics could be used as a part of incident response. This means that network forensics can be used to find many things regarding a case. Such as When incident occurred, How long incident occurred, How many systems were affected, What data was taken, also if the incident still going. Also, Network forensics could play a really important role in finding an evidence which could be used in court.
Speaking of evidence in network forensics, what is actually an evidence? According to Oxford English Dictionary. Evidence is information or signs indicating whether a
belief or proposition is true or valid. While the word Digital Evidence according to National Institute of Justice US means that Information stored or transmitted in binary form that may be relied on in court.
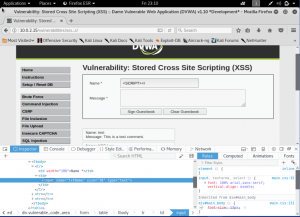
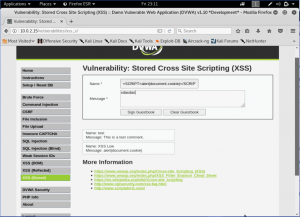
So, what are the sources for the evidence could be found in network forensics. Evidence for network forensics could be found on Network’s devices logs, Mirroring Network, ISP’s Logs, IP usage history, WiFI usage history, and CCTV/IP Based Camera.
Network forensics is a part of digital forensics which specific to network related. There are some challenges in network forensics such as questioning evidence admissibility and technical issue during acquisition evidence. Therefore, investigators must develop a
realistic strategy to meet the investigation goals and available resources.
With a methodology of investigation in network forensics will help investigators to perform network forensics and achieve investigation goals.